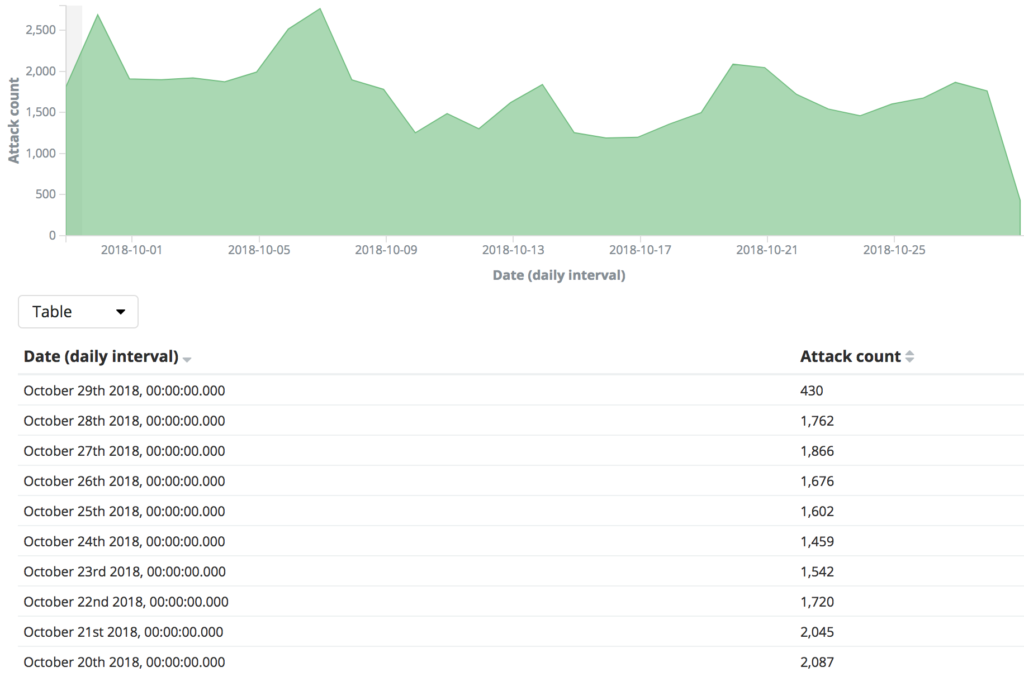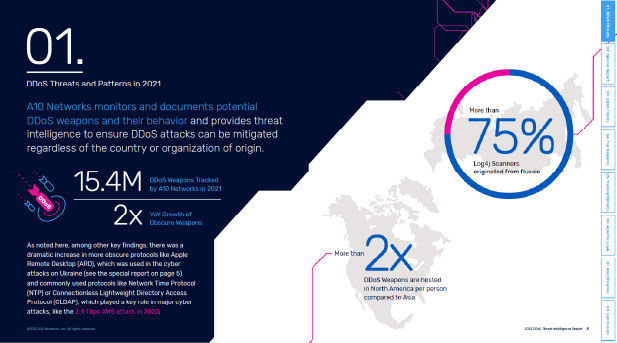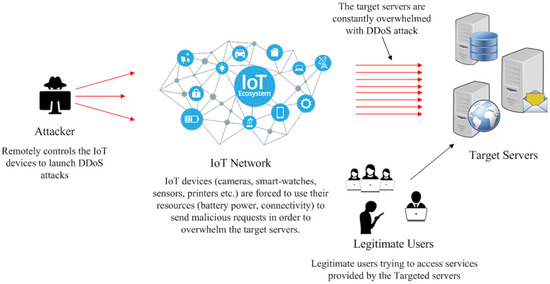
Sensors | Free Full-Text | Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm
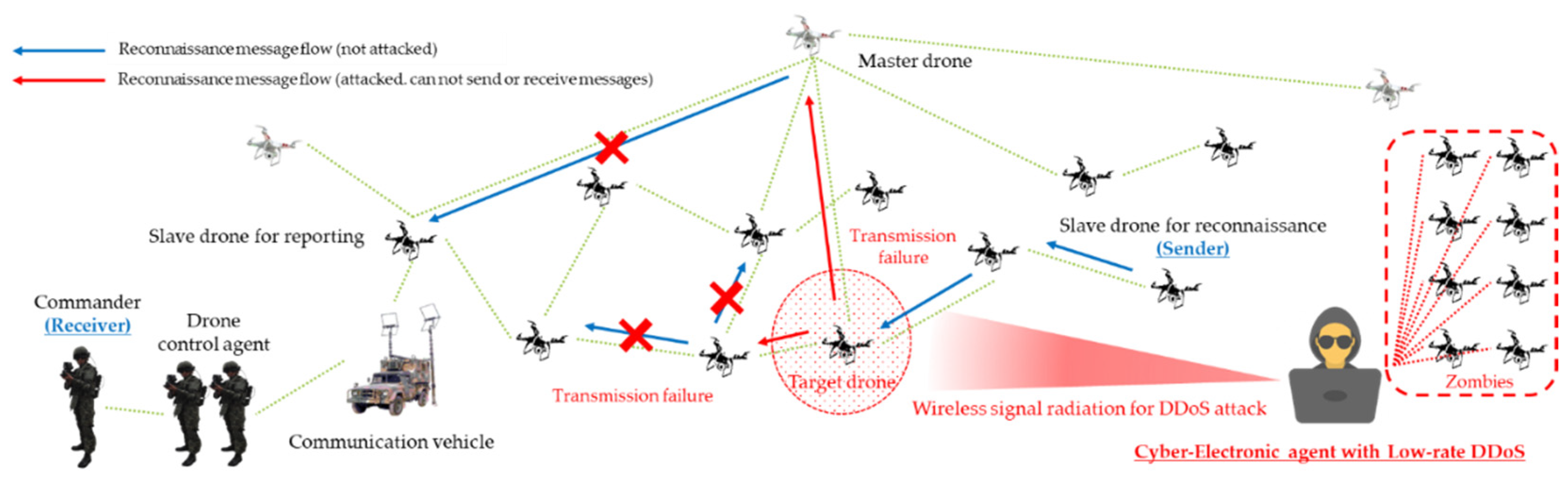
Sensors | Free Full-Text | D-CEWS: DEVS-Based Cyber-Electronic Warfare M&S Framework for Enhanced Communication Effectiveness Analysis in Battlefield | HTML

Sensors | Free Full-Text | D-CEWS: DEVS-Based Cyber-Electronic Warfare M&S Framework for Enhanced Communication Effectiveness Analysis in Battlefield | HTML

Concerns Security | Distributed Denial of Service Attacks | Moral Issues, Societal Factors Security Although distributed computing looks to provide an efficient means of conducting extraordinarily large scale computations, there are numerous privacy and ...
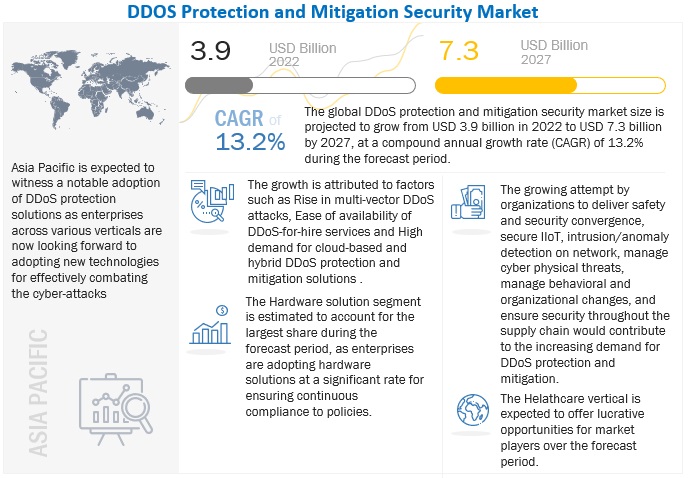
DDoS Protection and Mitigation Market Size, Share and Global Market Forecast to 2026 | MarketsandMarkets
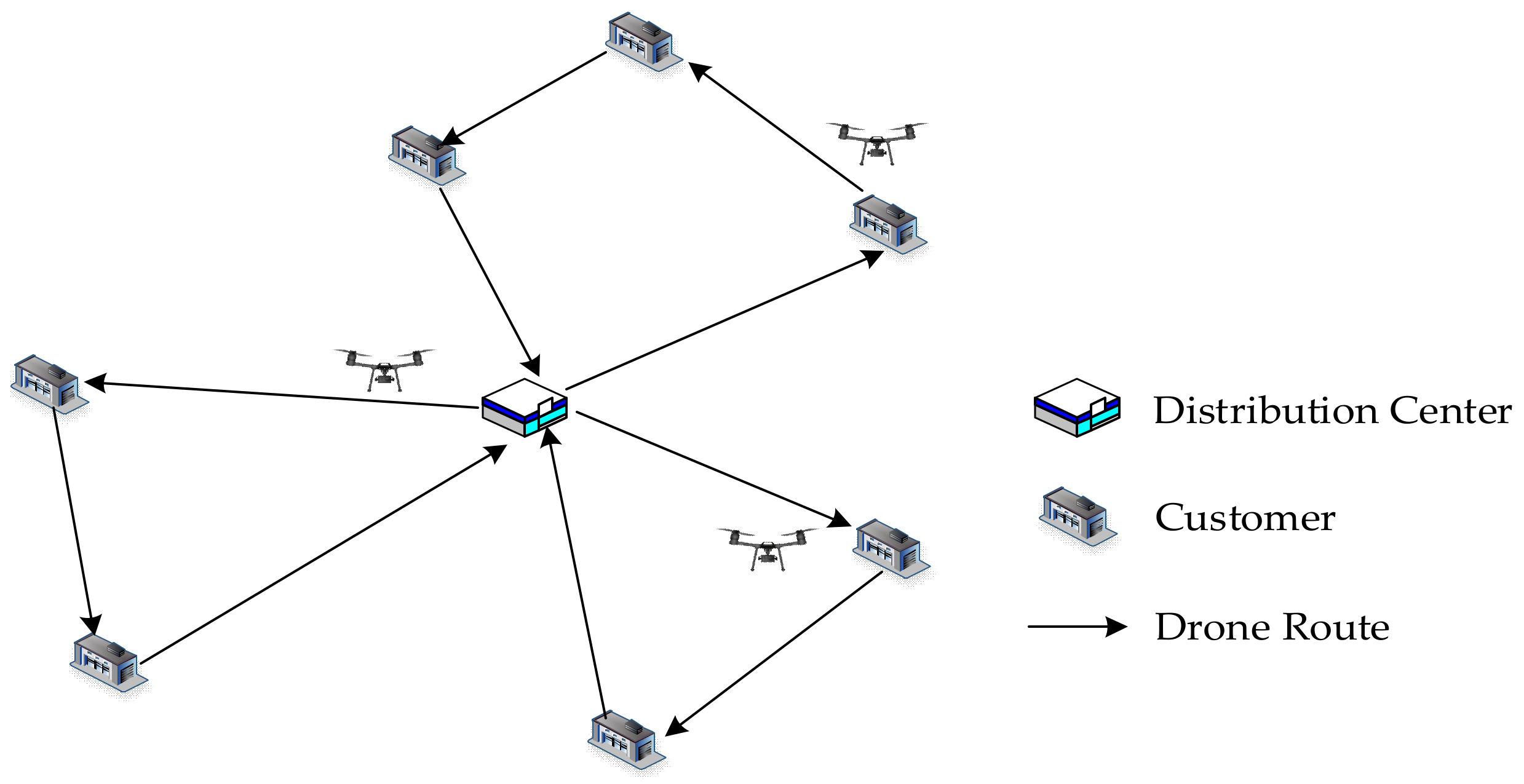
Sustainability | Free Full-Text | Optimal Model and Algorithm of Medical Materials Delivery Drone Routing Problem under Major Public Health Emergencies | HTML

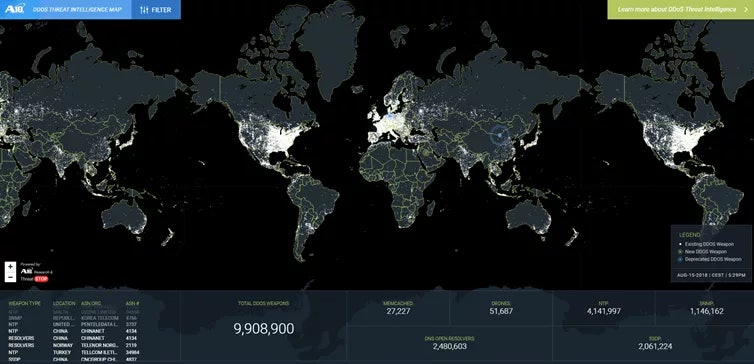
Run time variation with increasing number of UAVs for DDoS attack (same... | Download Scientific Diagram





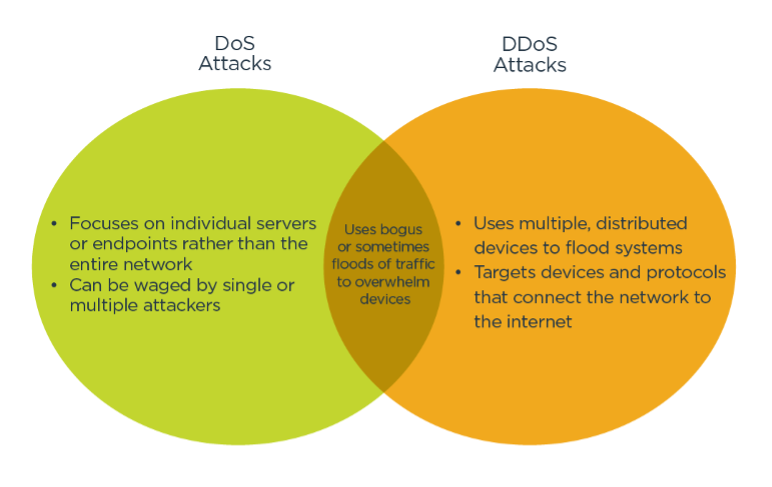


![Denial of service (DoS) attack [78] | Download Scientific Diagram Denial of service (DoS) attack [78] | Download Scientific Diagram](https://www.researchgate.net/profile/Phuoc-Dai-Nguyen/publication/349419829/figure/fig2/AS:1001946601238529@1615894093911/Denial-of-service-DoS-attack-78.png)