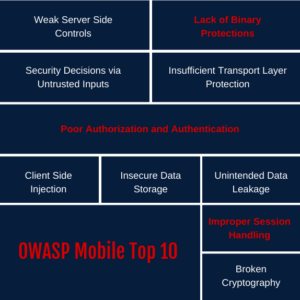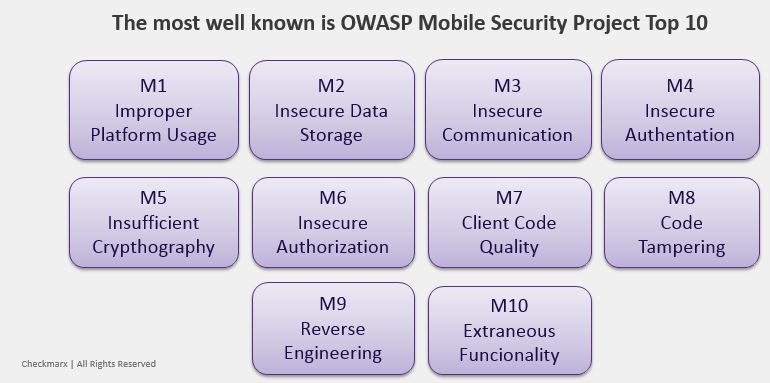
Hybrid versus Native Mobile App Development: Methodologies, Risks and Tools - Nova8 Hybrid versus Native Mobile App Development: Methodologies, Risks and Tools
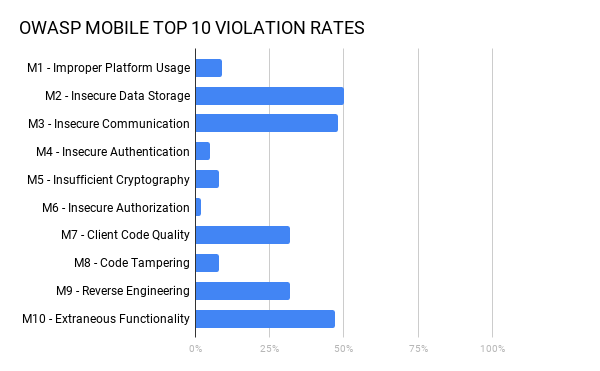
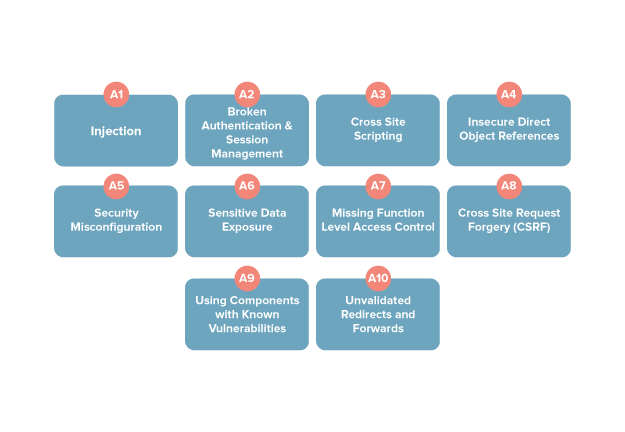
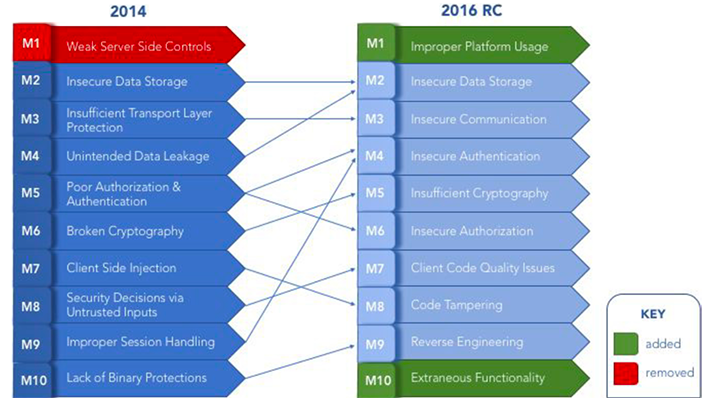
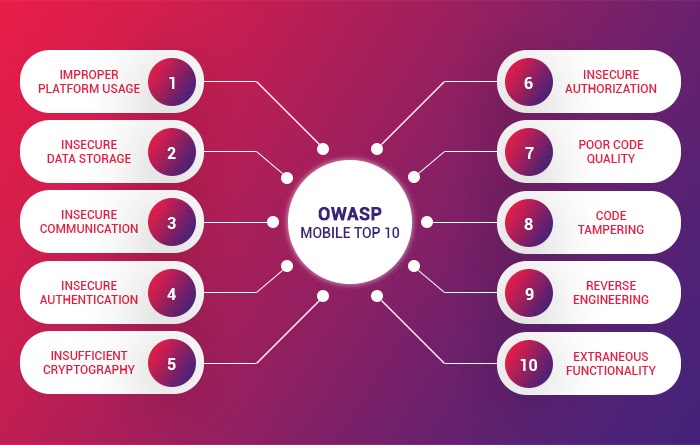
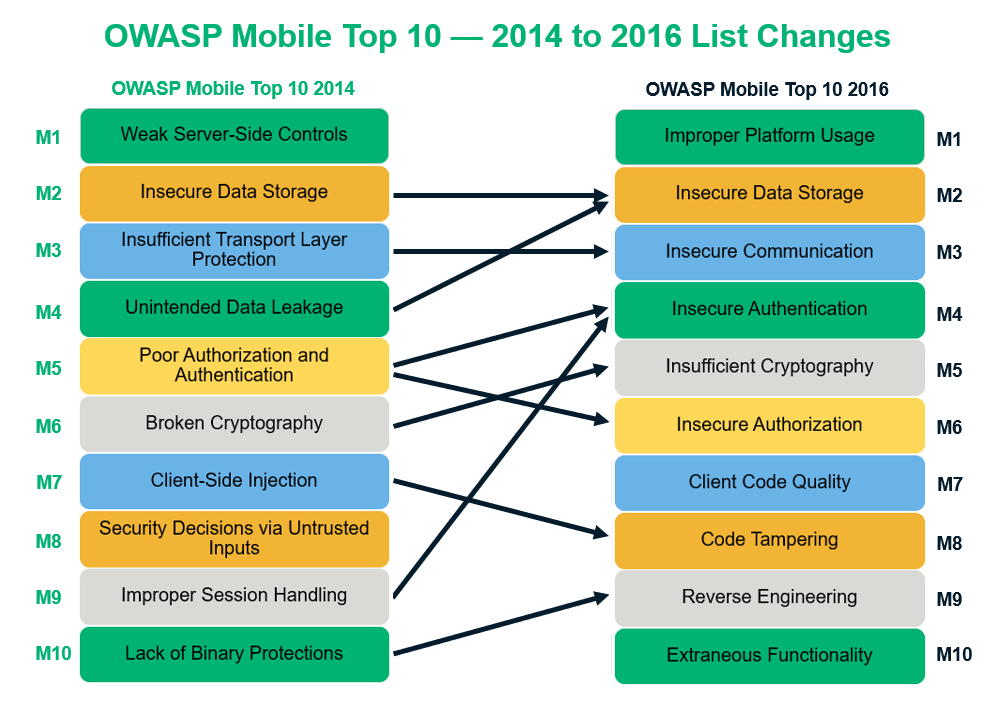
OWASP mobile top 10 security risks explained with real world examples | by Kristiina Rahkema | The Startup | Medium